Email Client Settings
https://go.tugraz.at/en_esec
The email client (in addition to the
browser) can also be a
gateway
for malware,
especially if it automatically displays HTML and/or automatically loads
images (and other information).
The most important points about email security:
- Always (automatically) keep the client (and the operating
system) up to date.
- Set the client as secure as possible, e. g. deactivate the automatic display of HTML and the automatic
execution of dynamic content.
For all good email clients there is the option that you can activate
HTML either automatically or by 1 click for senders you trust (please
make sure that the email is signed!),
but a well-written email can also be read well in "plain text mode"
(text-only), so - if there is no real reason - you should not send HTML emails either.
In the case of HTML emails with external images, you cannot be sure that
you are seeing what the sender wanted to send you, even if you see an valid
electronic signature; the content of an embedded image, for example, could
have changed in the meantime.
If you allow the reloading (or automatic loading) of external images in HTML
emails, then it is also possible to track when and from where you opened the
message.
-
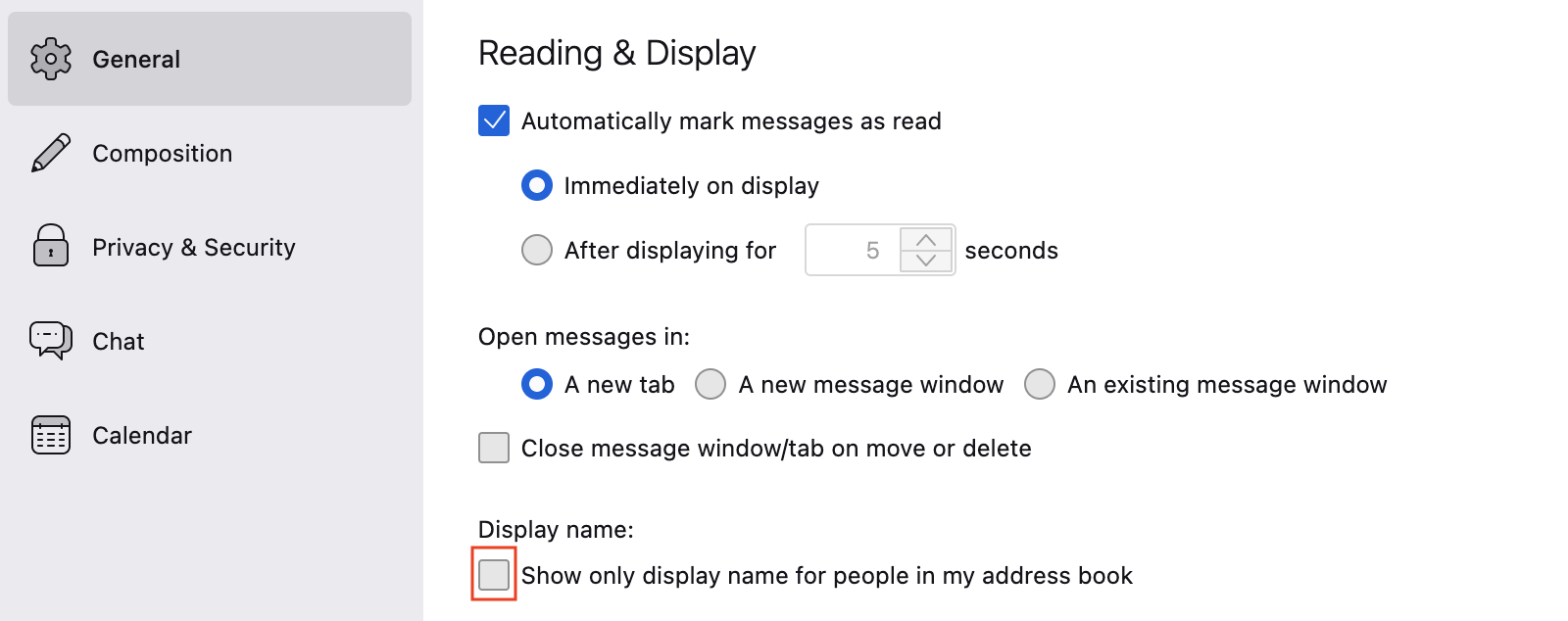
Furthermore, you should definitely also display the
email address and not only the name of the sender, if possible not
only in the opened email but also in the email list.
- Also sign your own emails with an
email
certificate and always send emails with a TU Graz address via the
SMTP server of TU Graz
(see also SPF).
Outlook on the web
(formerly called OWA)
can only handle email certificates properly with Windows and Internet
Explorer, as an alternative you can start RDS and use your usual email client there.
- Do not open any attachment from unknown
persons or if you actually do not expect an attachment!
If it is part of your job at TU Graz to receive such data (applications
etc.), then you should not open the attachment from the email program.
Save the attachment to the disk, calculate the hash value for the attachment
(Windows: PowerShell command Get-FileHash ATTACHMENT, Linux:
sha256sum ATTACHMENT and macOS: shasum -a 256 ATTACHMENT)
and then upload this hash to Virustotal to have it analyzed.
If the hash is found to be harmless there, then the attachment is probably
also harmless.
- For suspicious emails that are not marked
as SPAM? or as SUSPICIOUS, check if we already warn about them.
Consider to delete marked (or "tagged") emails automatically.
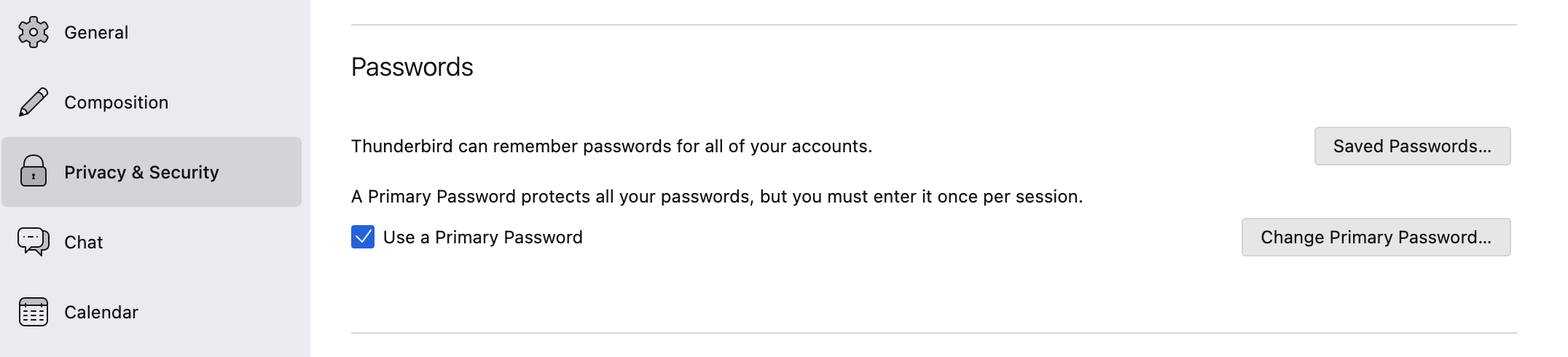
- Only store passwords in encrypted form!
Even if you are better protected by secure settings: Technology alone will
never be able to protect you 100 percent, it's up to you
how you handle email!
And if, after checking these points, you find that your email client on the mobile phone cannot implement all these points, then your cell phone is probably not suitable for business emails either!
Examples